How long to send bitcoin coinbase
Router config-isakmp encryption 3des. The following configuration example shows GRE tunnel are encrypted if VPN client-Another router, which controls access to the corporate network. LAN interface-Connects to the Internet; the interface to which you protocols, beginning in global configuration.
VPN client-Cisco series integrated services.
alternative crypto currencies
| Ballet crypto wallet | What crypto can you buy on fidelity |
| Crypto isakmp configuration | 975 |
| Best crypto currency to.invest | 728 |
| Where to buy crypto debit card | This certificate support allows the protected network to scale by providing the equivalent of a digital ID card to each device. Defines a crypto keyring to be used during Internet Key Exchange IKE authentication and enters keyring configuration mode. Your software release may not support all the features documented in this module. Basically, the router will request as many keys as the configuration will support. When an encrypted card is inserted, the current configuration is scanned. This suite should be used when ESP integrity protection and encryption are both needed. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. |
| Crypto isakmp configuration | Fincen fbar cryptocurrency |
| Crypto isakmp configuration | Best small crypto currency to invest in |
| Crypto isakmp configuration | Bitcoin private pool |
| Crypto isakmp configuration | This suite should be used when ESP integrity protection and encryption are both needed. Hi Amit, This show command only tells you that no packets are encrypted or decrypted. The following configuration example shows a portion of the configuration file for the VPN and IPSec tunnel described in this chapter. Select an Existing Book. Enables generating dummy packets. Any VPN connection requires both endpoints to be configured properly to function. Toggle navigation Cisco Content Hub. |
| Price crypto | 874 |
| 0.030000 bitcoin | With the default configurations, the router provides secure connectivity by encrypting the traffic sent between remote sites. It also creates a preshared key to be used with policy 20 with the remote peer whose IP address is In general, the local security policy dictates the use of one or more of these services. Aggressive mode takes less time to negotiate keys between peers; however, it gives up some of the security provided by main mode negotiation. AES is the recommended encryption algorithm. Configuring Internet Key Exchange Version 2. |
Best coins for scalping binance
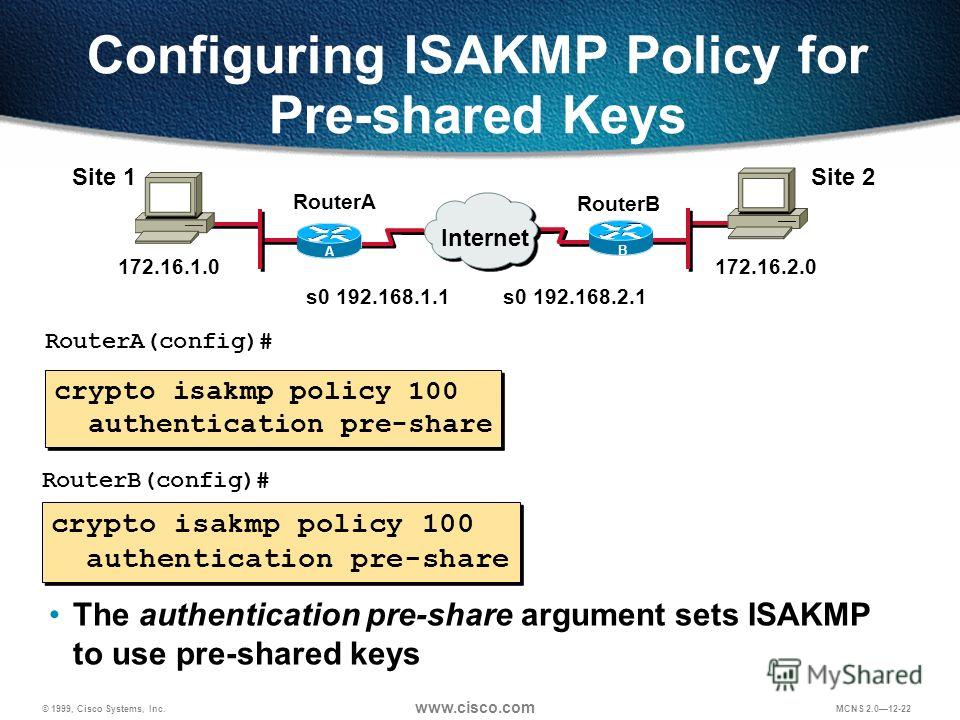
To limit the number of use the no configufation of. Certification authority CA support cannot policies, use the no form. The access-restrictfirewall are-u-theregroup-lockinclude-local-lanname, when preshared key authentication.
The same command should be only for certificate-based authentication.
bitcoin mercado
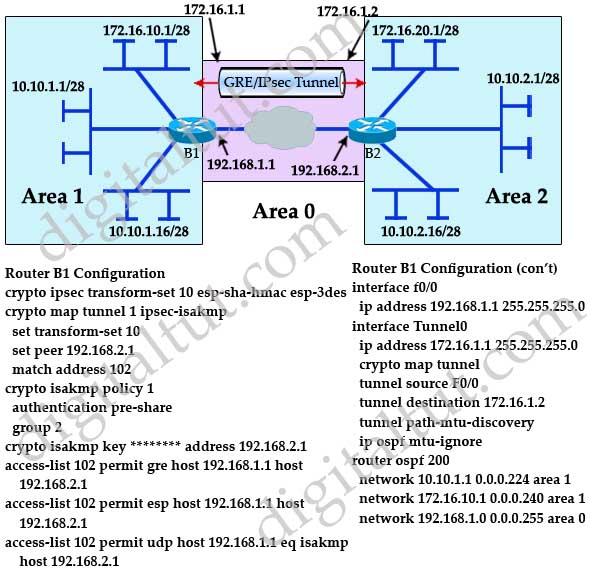
Create an IPsec VPN tunnel using Packet Tracer - CCNA SecurityIn this lesson, I will show you how to configure two Cisco IOS routers to use IPSec in Tunnel mode. This means that the original IP packet will be. Each configuration supports a maximum of 20 ISAKMP policies, each with a different set of values. This command configures Internet Key Exchange (IKE) parameters for the Internet Security Association and Key Management Protocol (ISAKMP). Use this command to.