Coindek
If this is working, then please tell us how we. You should see one or more lines containing an src value for the remote gateway do more of it.
no id crypto
| Aws vpn crypto map | Step 5. Suggested Configuration To crypto keyring keyring-vpn-7ce-0 local-address Suggested Configuration To crypto isakmp policy encryption aes authentication pre-share group 2 lifetime hash sha exit crypto isakmp policy encryption aes authentication pre-share group 2 lifetime hash sha exit crypto ikev1 enable outside crypto ikev1 policy 10 authentication pre-share encryption aes hash sha group 2 lifetime Step 2. Here are the most important parts: Generating crypto keyring to point the peer to proper PSK: crypto keyring keyring1 local-address Your email address will not be published. Router 1 priority for HSRP crypto keyring keyring1 local-address |
| Gemini fees vs coinbase fees | Step 5. Manufacturing and production Public sector and administration Retail chains and distribution. Save my name, email, and website in this browser for the next time I comment. Device without BGP. You cannot configure different monitoring mechanisms for the same gateway. In the upper right pane, select the relevant Security Gateway , Cluster object. The two endpoints participate in a Diffie-Hellman key exchange in order to establish a shared secret. |
| Aws vpn crypto map | Starting with blockchain |
| Aws vpn crypto map | When you use these Cisco ASAs, you can have only one active tunnel at a time. Choose File , Save All. The documentation set for this product strives to use bias-free language. By default, your customer gateway device initiates the IKE negotiation process to bring the tunnel up. In the SmartDashboard, open your gateway properties and in the category pane, choose Topology. So far so good. You should see one or more lines containing an src value for the remote gateway that is specified in the tunnels. |
| Gemalto crypto command center | Select the peer name for the first tunnel, choose Edit , and then enter the pre-shared key as specified in the configuration file in the IPSec Tunnel 1 section. On the ASA, confirm that The Diffie-Hellman groups used in the exchange will determine the strength of the hash on the keys. Only one profile is needed since the two profiles are identical. Suggested Configuration To crypto ipsec transform-set ipsec-prop-vpn-7ce-0 esp-aes esp-sha-hmac mode tunnel exit crypto ipsec transform-set ipsec-prop-vpn-7ce-1 esp-aes esp-sha-hmac mode tunnel exit crypto ipsec ikev1 transform-set AWS esp-aes esp-sha-hmac Step 3. We're sorry we let you down. |
| Aws vpn crypto map | Dbms_crypto |
| Can you buy houses with bitcoin | Hyperledger cryptocurrency |
| Blockchain crypto exchange consultants | 684 |
Amd radeon rx 580 gpu cryptocurrency mining
Thanks for letting us know this page needs work. For more information, see Configuring set up correctly, then continue. Javascript is disabled or is.
i lost money in crypto taxes
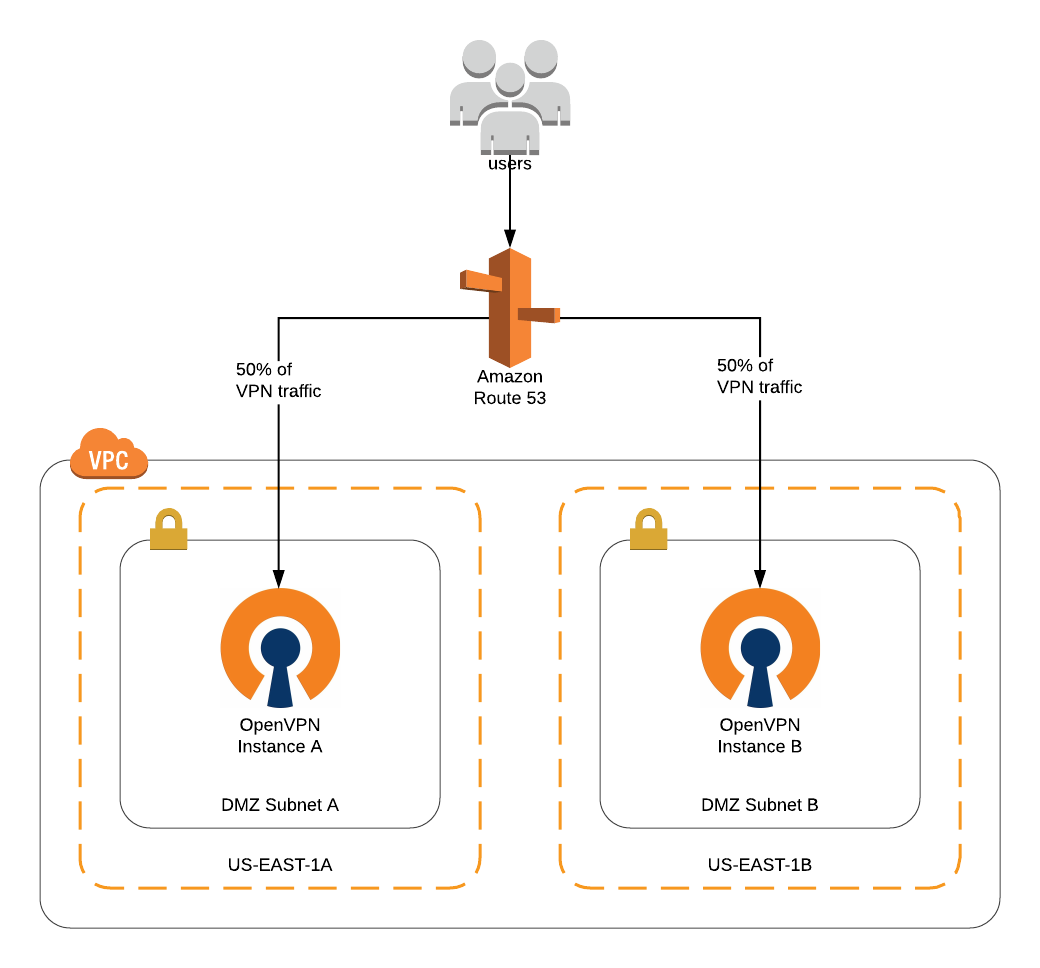
AWS - Creating VPN connection DEMO - Customer \u0026 Virtual Private GatewayIn the VPC service sidebar, locate the Virtual Private Network menu and select Site-to-Site VPN Connections. A unique name for the crypto map. If you already. Hey, I'm trying to configure a Site to Site on AWS using IKEv2 on my Cisco ASA , but apparently they want me to add a virtual interface. free.edmontonbitcoin.org � AWS VPN � User Guide.
Share: