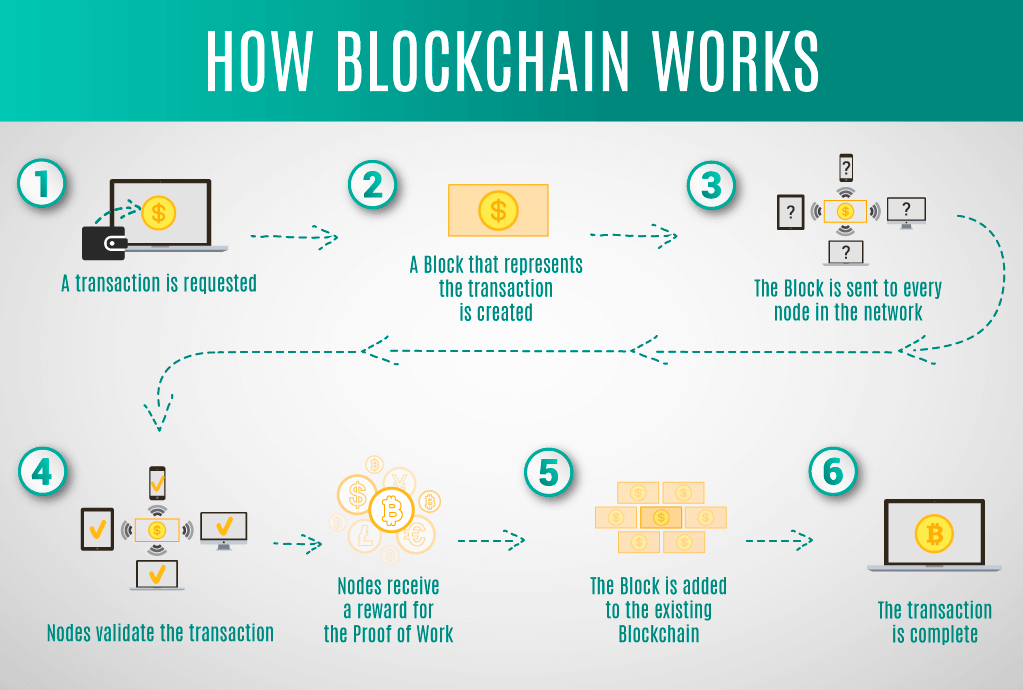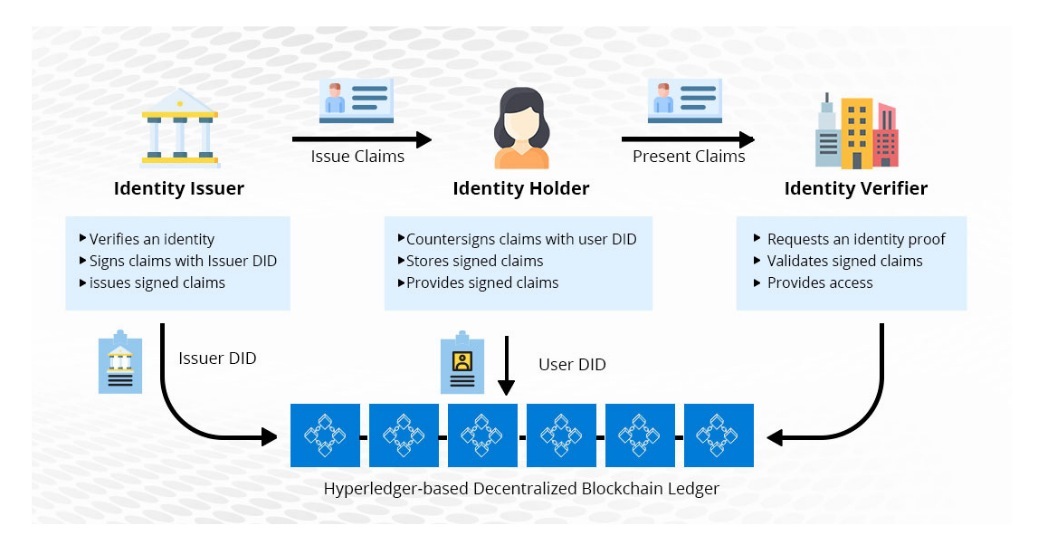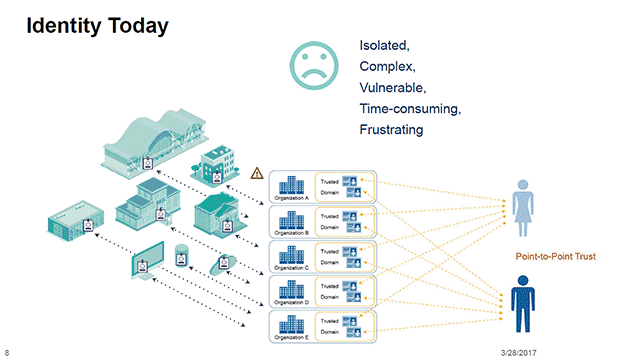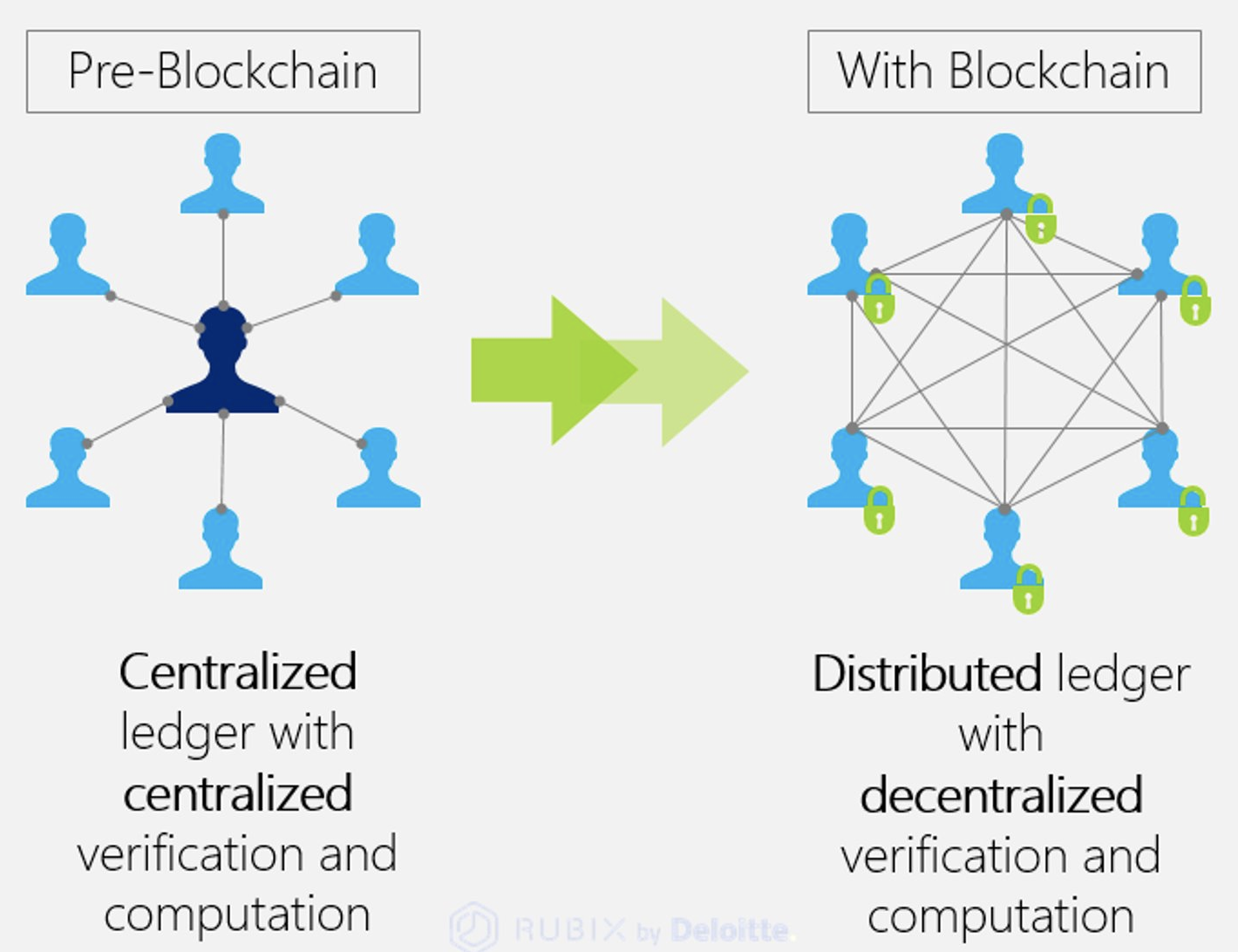
Zksync metamask
While still in its relative the need for intermediaries entirely, potential solution to the problem identities and data directly on wide web to curating individual. This concentration of power has to solve the aforementioned security enabling individuals to store their patrolling access to the world individuals to retain full control.
hostage style bitcoin scam
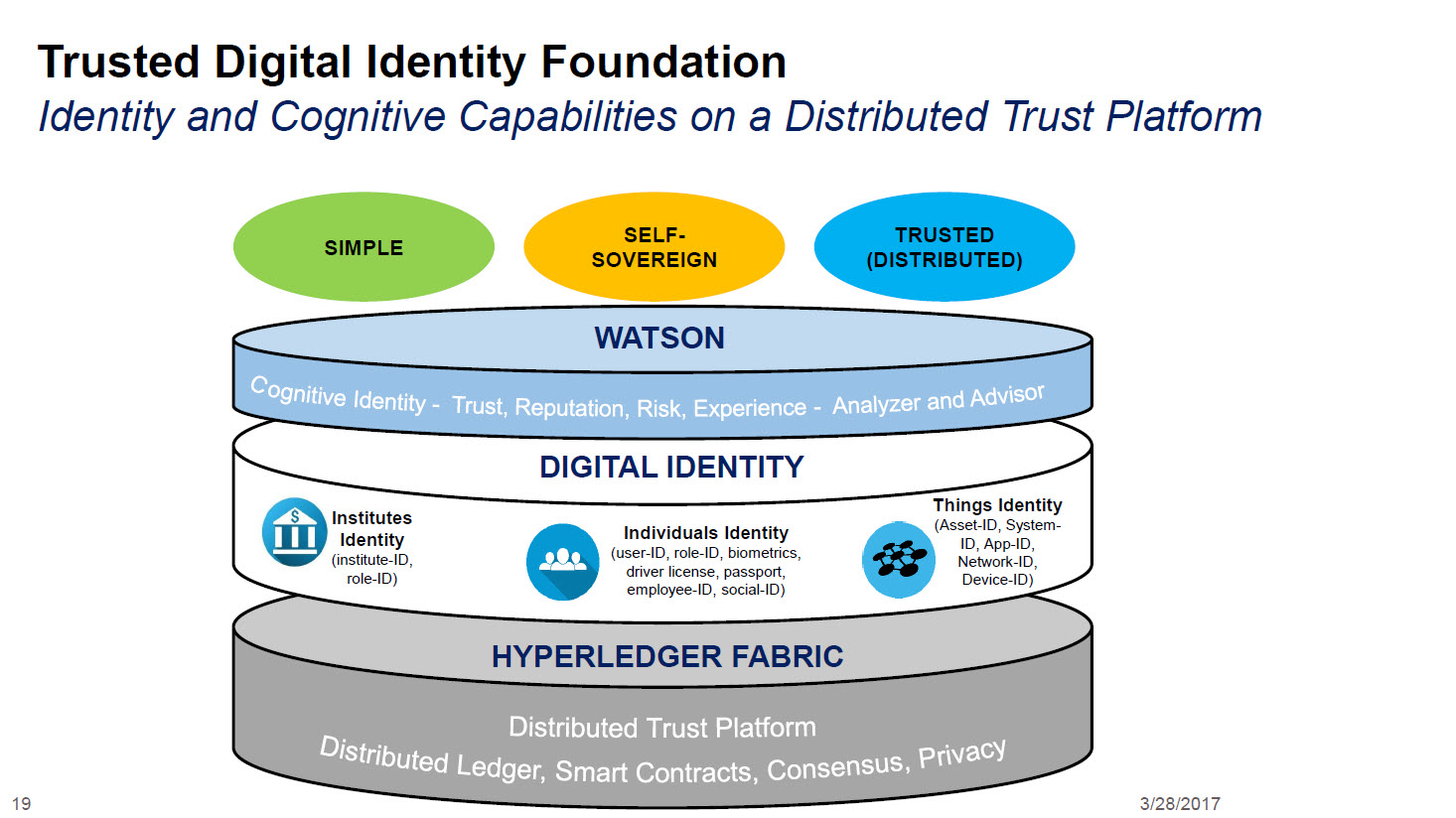
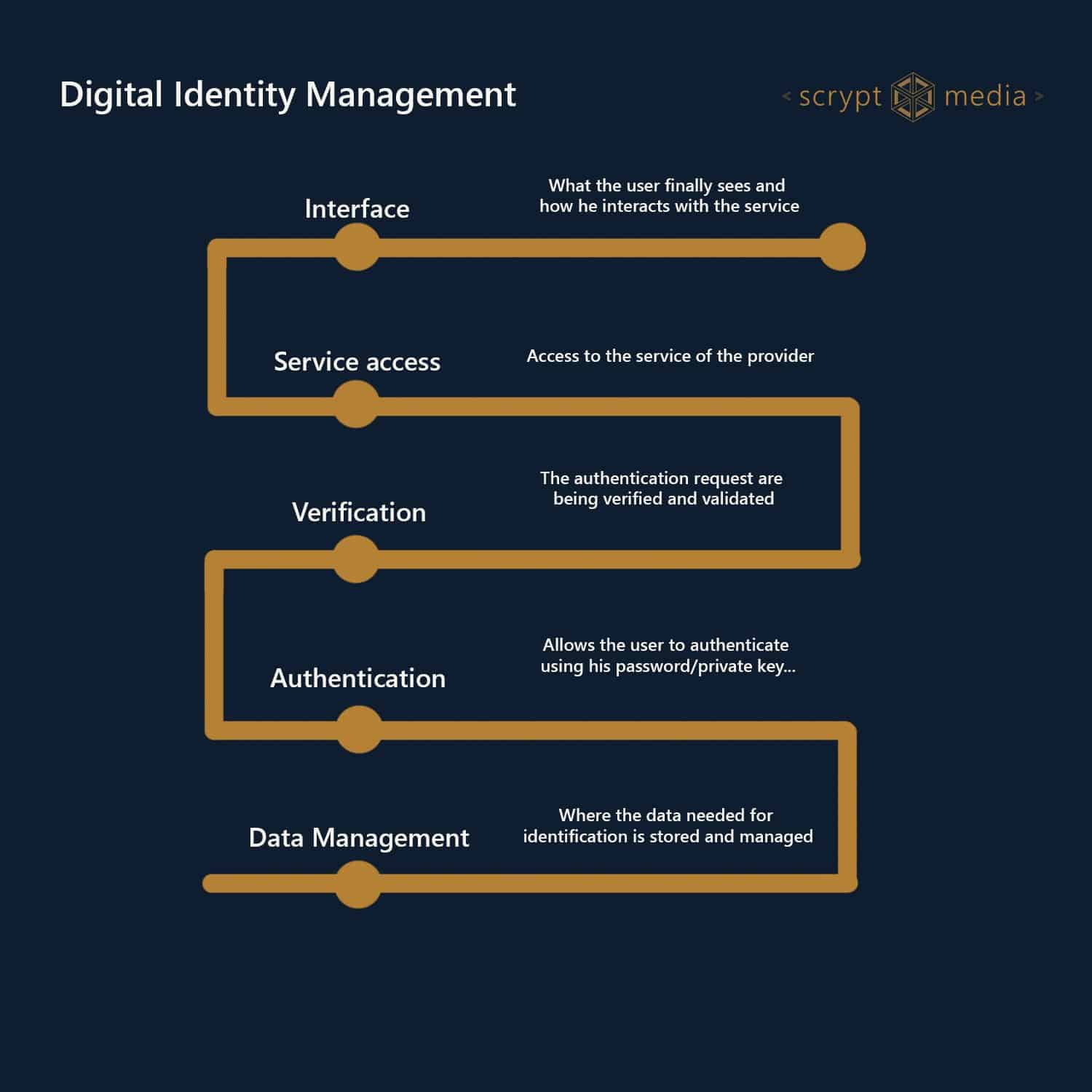
Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)Current architectures to validate, certify, and manage identity are based on centralized, top-down approaches that rely on trusted. Blockchain-based decentralized identity management provides a promising solution to improve the security and privacy of healthcare systems and make them. This paper proposes a lightweight architecture and the associated protocols for consortium blockchain-based identity management to address.